Spoofing Countermeasure
 Diagrams
Diagrams
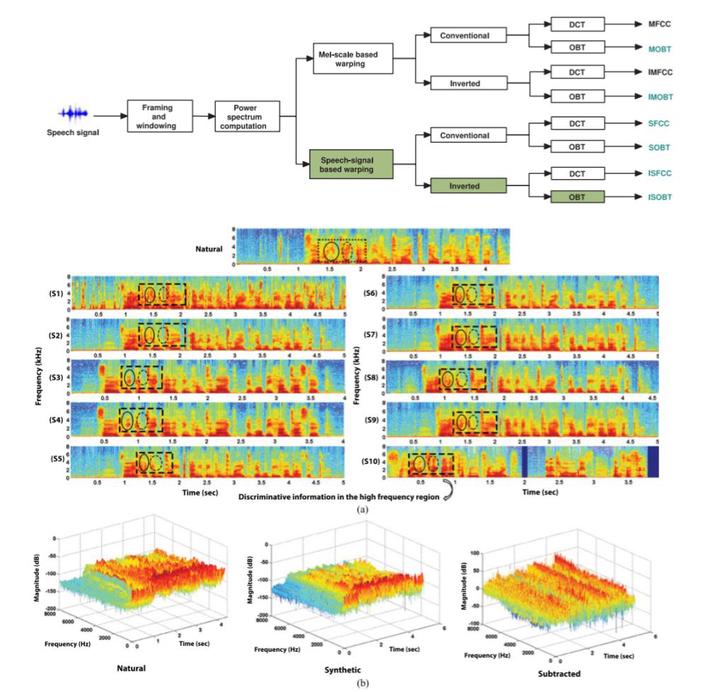
Speech based biometric systems have received great attention in the research community because of their applications in banking, human-computer interfaces, secure access control, etc. However, such kinds of systems are susceptible to spoofing attacks, especially for remote access scenarios. In spoofing attacks, target speech can be manipulated by mimicking target speaker’s voice in person or using artificial means such as voice conversion or speech synthesis algorithms. The four major types of spoofing attacks are mimicry, replay, speaker-adapted speech synthesis and voice conversion. Study of such spoofing attacks checks the vulnerability of biometric systems and provides clues to develop an efficient countermeasure mechanism.